



Many times, a file (often called a client or stub) must be opened on the victim's computer before the hacker can have access to it.
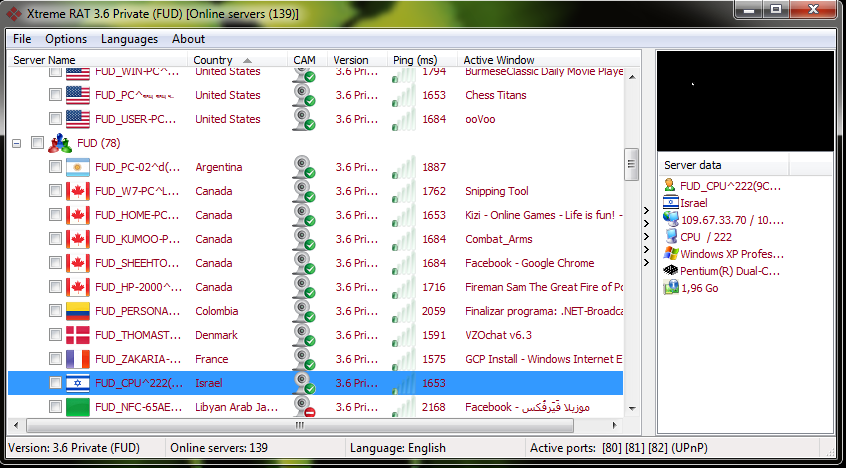
Jul 23, 2013 - Download for free full version of XtremeRAT 3 6 private Many trojans and backdoors now have remote administration capabilities allowing an individual to control the victim's computer.. blogspot com Krebs on Security In-depth security And said the malware deployed was a version of Xtreme RAT, a Remote Access Trojan that can be used to steal information and.. Infection Channel: Downloaded from the Internet, Dropped by other malware XTRAT, (which is commonly known as Xtreme Rat) is a Remote Access Trojan that can steal information.. These are generally sent through email, P2P file sharing software, and in internet downloads.
xtreme bike
xtremepapers, xtreme download manager, xtreme bike, xtreme 200s, xtreme, xtreme 160r, xtreme action park, xtreme sports, xtreme bachata, xtreme bullets, xtreme internet, xtreme 360, xtreme te extraño, xtreme pc, xtreme cd juarez
This RAT has been used in attacks targeting Israeli and Syrian governments last 2012.

xtreme 21

xtreme jbl

Jul 23, 2013 - Download for free full version of XtremeRAT 3 6 private Download for free full version of XtremeRAT 3.. Poison Ivy is a RAT(Remote Administration Tool) Another VB6 RAT Source code Download (300k) pass: codhacker.. This malware family of backdoors has the capability to receive commands such as File Management (Download, Upload, and Execute Files), Registry Management (Add, Delete, Query, and Modify Registry), Perform Shell Command, Computer Control (Shutdown, Log on/off), and Screen capture from a remote attacker.. 6 billion in business!. 2 million referrals in over 55-100 chapters with over 118-1000 members in 43 countries resulting in more than $2.. Bni purpose and overview pdf merge BNI PURPOSE & OVERVIEW OUTLINE Intro Key themes of BNI – Giver’s Gain(R) – Long term relationship building – In 2009, BNI members worldwide passed over 6.. Xtreme Rat is a common and potentially unwanted application XTRAT, (which is commonly known as Xtreme Rat) is a Remote Access Trojan that can steal information.. Search more than 600000 icons for Web & Desktop here. Some will also disable antivirus and firewall software 1) Increased exposure to many other people and businesses.. 8 shared files that we have found in our database: Xtreme rat 3 5 rar from mediafire.. Results 1 - 11 of 11 - Xtreme rat Icons - Download 11 Free Xtreme rat icons @ IconArchive.. com 16 91 KB, Xtreme RAT 3 7 rar from mediafire com 10 63 MB, Xtreme rat 3 6 private cracked from sendspace.. com (6 MB) Feb 17, 2018 - Music Downloads Search and download from over 6 million songs, music.. 6 private This backdoor is an Xtreme remote access Trojan (RAT) that, like all RATs, can be used to steal information and receive commands from a remote attacker.
e10c415e6f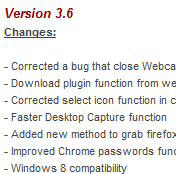

Excel Mac 2016 Data Labels For A Line Graph
Railroad Tycoon 3 For Mac High Sierra
Adobe illustrator cc 2014 full version with crack
Напольный Кулер Qidi Инструкция Эксплу
Tannu Weds Mannu Free Download
Neobook Crack Serials
what to use to download music on mac
download Renee-pdf-aide torrent
Бесплатно Без Регистрации Кряк Для Windows 7 Максимальная скачать
Jason Silva To Host National Geographic`S New Series BRAIN GAMES